Late one Friday afternoon, the owners of a small escrow firm in California logged into their bank account and felt their stomachs drop. Over a million dollars was missing, siphoned out in a series of international wire transfers. Within days, the 9-person business was forced to close its doors, its funds gone and no bank insurance to save it. This real-world nightmare isn’t a Fortune 500 story; it happened to a small- and mid-size business (SMB) much like any local business. If you run a small or medium-sized business, attacks like these show that cybercriminals won’t hesitate to target you.
With increased cloud adoption comes a growing need to safeguard data against sophisticated cyber threats. Attacks on cloud systems are climbing as more businesses move sensitive information off-premises. One recent study found 39% of businesses had a breach in their cloud environment in 2023, up from 35% the year prior. This trend shows that threat actors are aggressively probing cloud accounts, storage, and applications for weaknesses.
Whether you’re a business leader or an IT professional, understand the essential cloud security practices you must adopt. We’ll show you in plain English what threats you need to watch out for in the cloud and, more importantly, how you can protect your data effectively. The goal is to give you practical steps to defend your small business’s cloud assets, before you become yet another statistic in the cybercrime headlines.
Why Are Hackers Increasingly Going After SMBs?
In part, because many small business owners mistakenly believe “we’re too small to be on the hackers’ radar.” Yet nearly half of small businesses fell victim to a cyberattack in 2023. Criminals know SMBs hold valuable data from customer credit cards to health records but often lack the hardened defenses of large enterprises. It’s the digital equivalent of a burglar choosing a house with the doors left unlocked. In 2021, 61% of SMBs were the target of a cyberattack, and that proportion has only grown.
Attackers also bet that breaches in small firms will fly under the radar (no front-page news or FBI task force), making their odds of getting caught much lower. A couple of successful hits on small companies can be as lucrative as one big score on a giant corporation, with much less hassle.
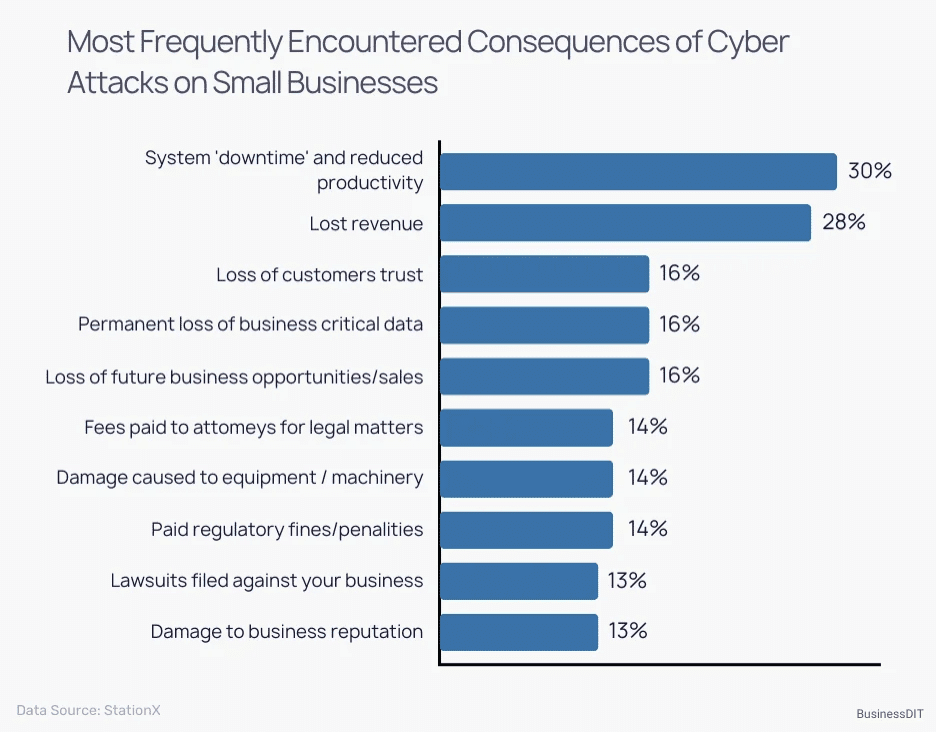
One recent industry survey highlighted the costly consequences SMBs face after a cyber incident. For example, 30% of small companies reported significant system downtime and lost productivity as a result of an attack, and 28% suffered direct revenue loss. Many also cited loss of customer trust, permanent loss of critical data, and legal fees among the fallout. These impacts help explain why an estimated 60% of small businesses hit by a cyberattack shut down within six months of the incident. In short, an attack can do more than just steal data–it can threaten your entire business.
Cloud security is not a “big company” problem alone. It’s a business survival problem. The point is not to scare you off the cloud, rather, to arm you with awareness. Remember, criminals will probe for any weakness, whether it’s technological (an open port, a weak API) or human (an employee reusing a password). A strong cloud security strategy is about covering those bases so attackers move on to an easier target.
What Are The Top Cloud Threats?
Moving data and applications to the cloud has huge benefits for SMBs, including ease of access, cost savings, and scalability, but it also introduces new security risks. Let’s break down the most critical cloud-related threats, and how they strike in real life:
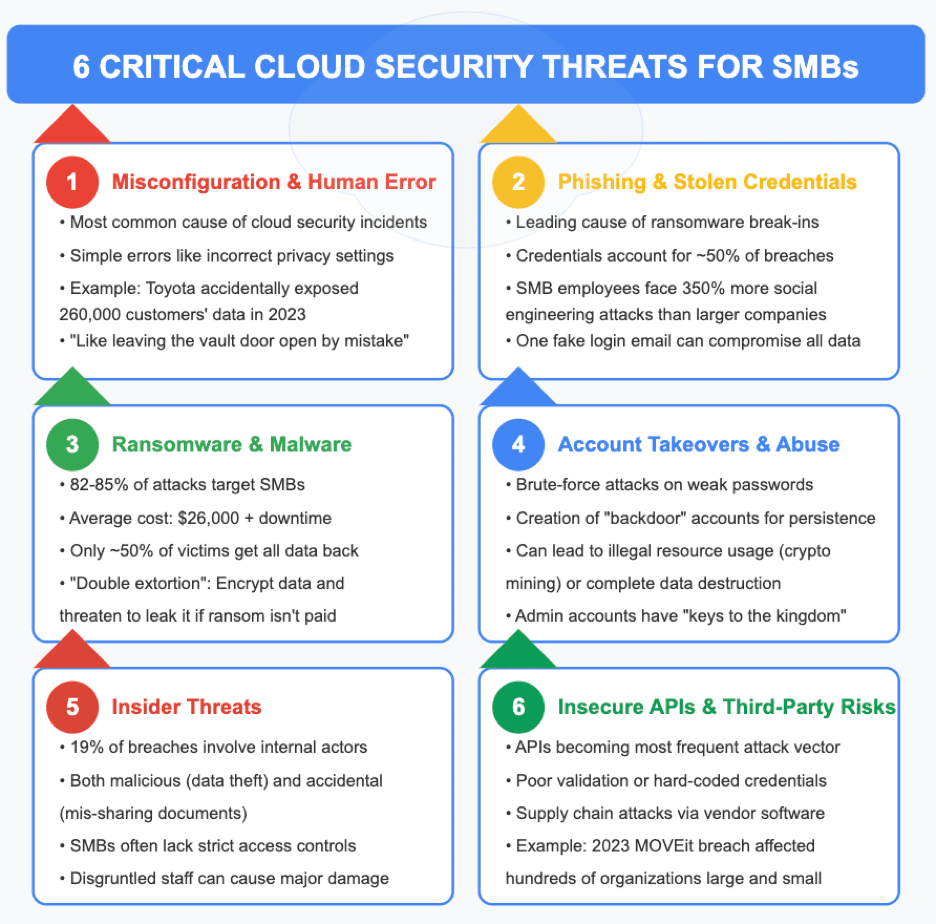
1. Misconfiguration and Human Error
One of the biggest security threats to cloud-stored data is not some elite hacker, but a simple mistake, like forgetting to set the right privacy setting on a storage bucket. Misconfiguration of cloud resources (storage, servers, databases, etc.) can inadvertently leave sensitive data exposed to the open internet. And this is incredibly common: studies find that the majority of cloud security incidents trace back to misconfigured settings or other human errors.
For example, in 2023 automaker Toyota accidentally left a cloud environment open and exposed 260,000 customers’ data online.
2. Phishing and Stolen Credentials
Phishing remains one of the top ways criminals pry open your front (virtual) door. In fact, phishing is the leading cause of ransomware break-ins (over half of ransomware attacks on small businesses start with a phishing email).
How does it work? Hackers send a convincing email that tricks someone into entering their cloud account password or multi-factor code on a fake site. Or they may steal credentials through malware on a PC. Once they have a valid username/password, they can login to your cloud apps just like an insider.
Verizon’s data shows that compromised credentials accounted for about 50% of breaches in early 2023. Attackers prey on the fact that smaller companies often have less training and may lack dedicated security staff watching for phishing attempts. All it takes is one employee falling for a well-crafted fake Microsoft 365 login email, and your cloud email or file storage could be in the hands of a thief.
3. Ransomware and Malware Attacks
Ransomware has not spared small businesses; in fact it targets them. Studies in recent years indicate that as many as 82–85% of ransomware attacks are aimed at organizations with under 1,000 employees.
The reasons are simple: smaller firms are more likely to pay (because they need their data back urgently and often lack backups) and more likely to have unpatched systems or single points of failure an attacker can exploit. Ransomware typically infiltrates via the aforementioned phishing or by exploiting a vulnerable system, then spreads to encrypt your files, including data you have in cloud drives or cloud backups if those are connected.
What’s worse? Even if you pay a ransom, there’s no guarantee you’ll get all your data back. One report found that after paying, only ~50% of SMBs got all their data restored, and in 27% of cases the attackers demanded additional money even after payment.
4. Account Takeovers and Cloud Account Abuse
Even aside from phishing, there are other ways attackers can hijack your cloud accounts. They might guess or brute-force weak passwords, or reuse credentials leaked from another breach.
If you’re not using multi-factor authentication, a hacker with the right password can waltz into your email, customer database, or cloud management console without resistance. Once in, they may create additional rogue users or “backdoor” accounts (so they can regain access even if the password is changed).
They could also change settings, for instance, lowering security configurations, or adding OAuth app connections to siphon data. Small businesses often don’t immediately notice such activity until the cloud bill arrives or systems start acting weird. Account takeovers are especially dangerous for SMBs because one admin or owner account. If that single account gets compromised, an attacker can potentially lock you out of your own systems or destroy data (as happened in the infamous Code Spaces incident, discussed later).
5. Insider Threats (Malicious or Accidental)
Not all threats come from outsiders. Employees or partners with legitimate access to your cloud data can pose a risk too, sometimes intentionally, sometimes by mistake. An angry or unscrupulous employee might download client lists from your cloud CRM to take to a competitor, or delete critical files in sabotage.
More commonly, an insider threat is unintentional: an employee might mis-share a sensitive document to “Anyone with the link” or upload company data to their personal cloud drive to work from home, inadvertently exposing it. According to Verizon’s analysis, about 19% of breaches involve internal actors, (the rest are external), and human error, misdelivery, misconfiguration, lost devices, etc., is a leading factor in many cloud data leaks.
The key is not to be paranoid about your team, but to recognize that anyone can make a mistake, and a disgruntled staffer or careless vendor with too much access can cause as much damage as a hacker if safeguards aren’t in place.
6. Insecure APIs and Third-Party Integrations
Modern businesses rely on a web of cloud apps that talk to each other via APIs (Application Programming Interfaces). For instance, your billing system might use an API to pull data from your e-commerce site. These connections improve efficiency but can introduce vulnerabilities. If an API is poorly secured (e.g. using hard-coded credentials, or no rate limiting), attackers can exploit it to extract data or perform unauthorized actions. Gartner famously predicted that by 2022, APIs would become the most-frequent attack vector for breaches, and indeed, we’ve seen a surge of API-related breaches in recent years.
For an SMB, an API breach might look like this: your website’s contact form API inadvertently lets someone inject code or retrieve all your customer queries because of a validation flaw, or a trusted third-party plugin has an API that gets hacked and becomes a conduit into your data. The massive 2023 MOVEit breach (a compromised file transfer cloud tool) impacted hundreds of organizations large and small.
SMBs often use many third-party cloud services and assume they’re secure, but if any one of those gets breached, your data could be collateral damage.
These are some of the top threats you face when leveraging cloud platforms. Each threat described above has effective defenses, which we’ll explore next.
What Can You Do To Protect Cloud Data?
Are you thinking, “what can I actually do about it, given my limited time and budget as an SMB?” The good news is that you don’t need a giant SOC (Security Operations Center) or a team of PhDs to substantially improve your cloud security. Small businesses can take a series of practical, often low-cost steps to dramatically lower the chances of a breach.
Let’s walk through these strategies, so you can see how they fit into your day-to-day operations:
Start with Smart Cloud Setup, a.k.a. Encryption Everywhere
Imagine you’re uploading your company’s financial records or client files to a cloud storage service like Dropbox, Google Drive, or Amazon S3. Before you even hit “Upload,” make sure that data is encrypted both at rest and in transit.
What is encryption? It’s like turning your sensitive information into gibberish for anyone who doesn’t have the key. Most reputable cloud services offer built-in encryption, often you just need to ensure it’s enabled. For example, AWS S3 allows you to enforce that all objects are encrypted on disk.
Also, always use HTTPS or a VPN for data in transit so that when you or your employees connect to cloud systems, the information isn’t exposed en route. A 2023 study found that while more companies are storing sensitive data in the cloud, only about 45% of that cloud data is encrypted, so by doing this, you’re already ahead of many.
How does it help? If a hacker somehow gains read access to your storage (through misconfig or insider mishandling), encryption means they can’t actually read your files without the proper keys. It’s an essential last line of defense. In short: flip the encryption switch wherever possible, and you instantly make your cloud data much harder for any thief to exploit.
Lock Down Access with Strong Authentication
Do you recall from above that about half of breaches come from stolen credentials? The obvious fix is to strengthen your authentication, i.e. how you and your team log in to cloud accounts. The single most effective measure is enabling multi-factor authentication (MFA) on every account that supports it. MFA adds a second step (like an app code, text message, or hardware token) after the password. It’s like requiring two keys to open a lock instead of one. This stops the vast majority of automated hacking attempts in their tracks. In fact, Microsoft observed that 99.9% of compromised accounts did not have MFA enabled, essentially, almost all account hijacks can be prevented by this one security measure.
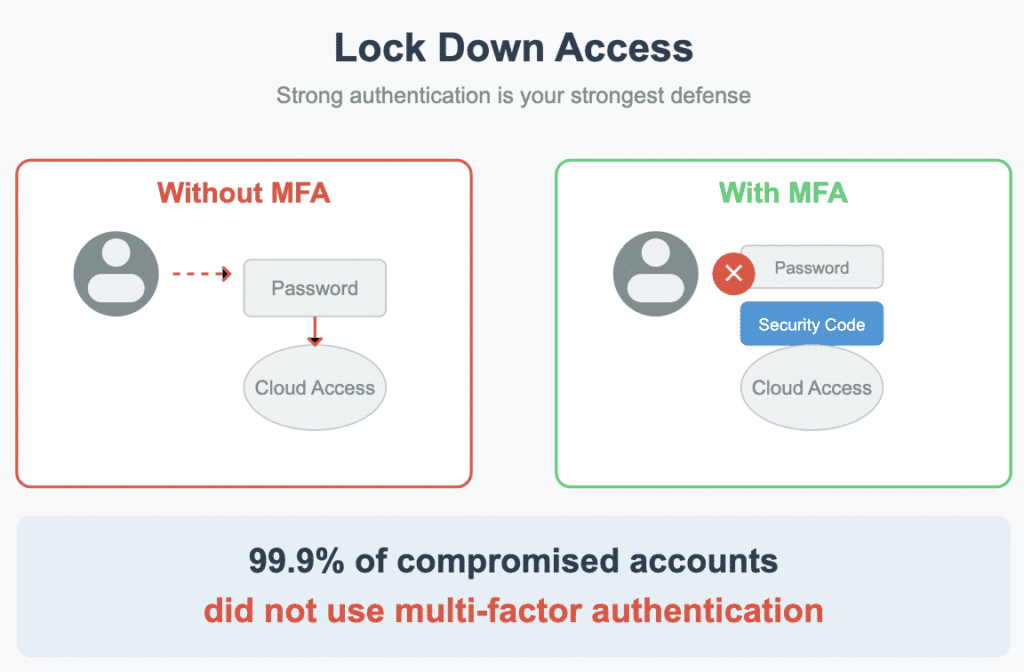
Many services let you enforce it as an administrator. Yes, it adds one more step for your employees at login, but the protection is well worth it. Along with MFA, ensure everyone is using strong, unique passwords–no more “Summer2023!” reused on multiple sites. Consider a password manager to help your team manage unique passwords without frustration. Also, promptly remove access for ex-employees or contractors and don’t share accounts if possible.
These basic access control hygiene steps will foil both casual hackers and targeted attacks–because even if attackers phish a password, they’ll be stopped cold by that second factor.
Follow Principle of Least Privilege
A fancy term with a simple idea – give each person and system the minimum level of access needed to do their job, and no more. In practice, review who can access what in your cloud environment.
Does your part-time marketing contractor really need full read/write access to all your customer data? Probably not.
Use your cloud platform’s access control tools to set role-based permissions. For example, in AWS or Azure, don’t use root or admin accounts for everyday work – create limited IAM users. In Google Drive or SharePoint, set up folders with permissions so only HR can see the “HR Records” folder, etc.
This way, if one user’s account is compromised, the hacker can only reach the subset of data that user was allowed to see. Likewise, if an employee goes rogue or makes a mistake, the blast radius is limited.
Take Regular Backups (and test them)
Imagine for a moment that tomorrow ransomware strikes and all your cloud-stored data becomes encrypted gibberish. Or a disgruntled employee wipes crucial files. Would you still have your customer records, financial info, or project documents?
You must have backups of critical cloud data. Many cloud services don’t automatically back up your stuff in a way you can easily retrieve (they often rely on you to configure backups or retention). So, take control of your backups.
For files in services like Google Drive/OneDrive, periodically export and save an extra copy offline or in another secure cloud. For cloud databases or virtual machines, use the provider’s snapshot or backup features to take regular backups (daily or weekly, whatever makes sense) and store those backups in a separate account or location.
The key is to also store backups isolated from your main environment, so an attacker who gets into your network can’t just encrypt or delete the backups too. This might mean keeping an offline copy (e.g. on an external hard drive stored safely) or using a different cloud account just for backup storage. And don’t forget to test restoring those backups once in a while!
Backups are your insurance policy–relatively cheap and boring, but absolutely invaluable when you need them.
Monitoring and Alerts
In the physical world, businesses use alarm systems and CCTV to detect break-ins. In the cloud world, you should similarly set up monitoring and alerts for suspicious activity. The great thing about cloud platforms is they usually log everything–logins, file downloads, changes made–and many have built-in alerting you can configure.
For example, Microsoft 365 and Google Workspace can send you an alert if there’s a logon from a new country or if a user suddenly deletes a ton of files. There are also third-party security services (including affordable ones for SMBs) that can watch your cloud accounts for unusual patterns (like an employee logging in at 3 AM and attempting to access hundreds of files).
As a small business owner, you likely can’t watch logs 24/7, but you can set up email/SMS alerts for high-risk actions. Even something as simple as receiving an alert when an admin account logs in, or when a new device connects to your cloud storage, can tip you off and prompt a quick response. And if you do get such an alert or notice something odd–investigate immediately.
By implementing basic cloud monitoring, you turn on the lights and security cameras in your environment. Attackers hate that–it increases their risk of being caught, and they often move on if they suspect an organization is watching for them.
Educate Employees and Update Policies
Your employees can be your weakest link or your first line of defense. A bit of regular security training goes a long way in preventing incidents.
- Teach your team how to spot phishing emails–those strange “urgent” emails asking them to click a link or provide a password.
- Make it clear that it’s always OK to double-check with IT or their manager if an email seems suspicious.
- You can even run simple phishing drills (services can send test phishing emails to staff to see if anyone clicks – a great way to identify who might need extra training).
- Beyond phishing, ensure everyone knows the basics: don’t reuse corporate passwords on other sites, don’t install random software or browser extensions, and be cautious when connecting to public Wi-Fi (use a VPN if needed when on the road).
- It’s also wise to have an acceptable use policy and basic procedures, for example: “We do not send sensitive data over email without encryption” or “All company laptops must have up-to-date antivirus and full-disk encryption.” Keep the rules simple and understandable.
For a small business, even quarterly 30-minute security refreshers or a shared funny security video can keep awareness up. Remember, one careless click by an employee can undo a lot of other security efforts, so invest in your people’s cyber savvy.
Incident Response Planning
While not as exciting as new tech, having an incident response plan is crucial. This is basically a playbook for “what do we do if something goes wrong?” Many SMBs don’t think about this until they’re in the middle of a crisis, which is not ideal.
Take some time to outline steps for different scenarios – e.g. if a laptop is stolen, who should be notified and what actions to take (remote wipe, change passwords); if we suspect a breach, who do we call (IT consultant, cyber insurance, law enforcement?), how do we communicate internally and to possibly affected customers, etc. Even a one-page checklist is better than nothing.
As part of planning, build relationships with external experts before an incident if you can – e.g. know a local IT security firm or consultant you could call in a pinch. And ensure you have key info handy like emergency contact numbers for your cloud providers (many have 24/7 support in case of security issues) and access to critical accounts (you don’t want to be scrambling for the admin password to your server during an incident). SMBs that respond swiftly to attacks (within hours) can often avoid turning an incident into a full-blown disaster.
Compliance and Cloud Security
Finally, protecting data isn’t just a good practice, in many industries, it’s the law. While this could be a whole guide in itself, be aware of any compliance requirements that apply to your business and cloud usage.
For example, healthcare providers must follow HIPAA, which has specific rules for handling electronic Protected Health Information (ePHI) – including using cloud services that will sign a Business Associate Agreement (BAA). Retailers who accept credit cards fall under PCI DSS standards – if you use a cloud-based point of sale or e-commerce system, you need to ensure it’s PCI compliant (e.g. proper network segmentation, no stored plain card numbers, etc.).
The key takeaway here is: know the rules for your industry and verify that your cloud security measures meet those. Often, the best practices we’ve discussed (encryption, access control, monitoring) map directly to compliance requirements. You might also consider industry-specific security certifications or audits down the line to build trust with clients (for example, some SMBs pursue SOC 2 certification or follow NIST guidelines to show their data protection posture).
Industry Specific Security Considerations For Cloud Data
Every business has unique data and regulations. Below are a few examples of how cloud security might look for you in various industries. See which scenario sounds like yours:
Industry: Healthcare (Clinics, medical practices, etc.)
Risk level: VERY HIGH
In the U.S., healthcare faced a staggering 128% increase in cyber attacks in 2023, making it the most-breached industry that year.
Why Attackers Target Healthcare? Healthcare organizations are prime targets because they hold:
- Extremely sensitive personal medical records, and
- Systems critical for patient care (making them more likely to pay ransoms)
Key Compliance Requirements
| Regulation | What It Means For You |
| HIPAA | Requires safeguarding protected health information (PHI) |
| BAA | Business Associate Agreement must be signed with any cloud provider |
For a small healthcare practice using cloud services (say, a cloud-based electronic health record system), compliance with HIPAA is paramount. This means you should only use cloud providers that will sign a HIPAA Business Associate Agreement, ensuring they follow required security controls. Here are some essential security measures you can take:
- Multi-factor authentication is a must for accessing patient data (to prevent account hacks)
- Audit logs should be enabled to track who accessed what record and when (HIPAA requires audit trails)
- Maintain regular data backups for all patient records
- Develop an incident response plan that includes HIPAA-mandated breach notification procedures
In healthcare, it’s not just about protecting data for its own sake – it’s about protecting your patients and maintaining their trust. A small orthodontist’s office or neighborhood clinic might not think they’ll be targeted, but the stats say otherwise.
Industry: Financial Services (Accounting Firms, Financial Advisors, etc.)
Risk level: VERY HIGH
Financial services suffers the second-most data compromises (just behind healthcare).
Why Attackers Target Financial Services? Financial organizations attract cybercriminals because they:
- Handle direct access to money and financial assets
- Store valuable personal information that can be used for identity theft
Key Compliance Requirements
| Regulation | What It Means For You |
| GLBA | Requires protection of customer financial data privacy |
| PCI DSS | Mandates security for credit card processing |
Finance is another high-risk, highly regulated sector. Whether you’re a local credit union, a mortgage broker, or a CPA using cloud-based accounting software, you deal with money and therefore attract cybercriminals like moths to a flame. Attackers might try to steal bank account numbers, initiate fraudulent transactions, or harvest personal info for identity theft. Some security measures that become essential for you include:
- Implement strong access controls (for example, limit who can see full credit card or SSN fields in your cloud systems)
- Ensure robust network security (use firewalls, VPNs for any connections to cloud financial apps)
- Enable encryption of data at rest and in transit as a standard
- Verify cloud providers have relevant security certifications (SOC 2, ISO 27001)
- Establish verification procedures for fund transfers to prevent Business Email Compromise
Financial regulators also expect firms to have an incident response plan and to report breaches to authorities and possibly customers in a timely manner. Additionally, be wary of Business Email Compromise (BEC) scams. In this, a hacker might spoof a client’s email and trick you into wiring funds to the wrong account. Having verification procedures (e.g. always confirming large fund transfer requests via a phone call) can thwart that.
Industry: Retail and eCommerce
Risk level: HIGH
Retail businesses, especially those selling online, face security issues both in-store and in the cloud.
Why Attackers Target Retail? Retail businesses are attractive targets because they:
- Process large volumes of payment card data
- Often have less sophisticated security than financial institutions
Key Compliance Requirements
| Regulation | What It Means For You |
| PCI DSS | Sets standards for handling payment card data |
| GDPR/CCPA | May require specific customer data protections depending on location |
If you run a small online shop or even a brick-and-mortar store that uses cloud-based point-of-sale systems, consider that customer payment data is your crown jewels. Hackers might target you with credit card skimmers (malware that siphons card numbers during transactions) or by hacking your e-commerce platform to steal your customers’ personal and payment info. Here are some security measures you need to take to protect transaction security and customer accounts:
- Use payment processors that handle sensitive data storage (minimizing your exposure)
- Keep all payment software updated to patch vulnerabilities
- Implement network segmentation (customer Wi-Fi should be separate from POS systems)
- Offer multi-factor authentication options for customer accounts
- Implement fraud detection systems to prevent credential stuffing attacks
- Maintain regular backups of product and order databases
On the compliance side, if you operate in places with privacy laws (GDPR in Europe, CCPA in California, etc.), be mindful of how you store customer data in the cloud–you may need to provide deletion of data upon request or disclose if data is going to third parties.
Retail often sees a lot of credential stuffing attacks–where attackers use lists of stolen passwords to try to log in to customer accounts on your site.
Industry: Legal Services and Other Professional Firms
Risk level: HIGH
Roughly 4 in 10 law firms experienced a security breach, a statistic that should make any attorney take notice.
Why Attackers Target Legal Services? Law firms and professional services are targeted because they:
- Hold confidential client business information and intellectual property
- Possess sensitive personal data that could be used for various schemes, even to sell to other nation-states
Key Compliance Requirements
| Consideration | What It Means For You |
| Ethical Obligations | Professional responsibility to protect client confidentiality |
| Industry-Specific Laws | May vary based on the specific professional service |
Law firms, consulting agencies, and other professional service SMBs might not think of themselves as obvious cyber targets, but they absolutely are–primarily because of the sensitive data and client secrets they hold. Here are some measures that can protect their cloud data:
Restrict access to client files only to staff working on specific cases
- Use reputable cloud vendors with strong security records for case management
- Implement encryption for all client communications and data storage
- Conduct regular security awareness training (lawyers are prime phishing targets)
- Monitor for unauthorized access attempts to sensitive client information
- Establish clear data handling procedures for client intellectual property
Beyond general good practices, legal and professional firms should be aware of any ethical or contractual obligations. If you deal with any personal data of consumers, privacy laws might apply – attorney-client privilege doesn’t exempt you from, say, reporting a breach of personal data under state law.
For other professional services (marketing agencies, design firms, etc.), the concerns are similar if you host client data.
Whatever industry you’re in, a common thread is that compliance requirements often mirror best practices. If you’ve implemented the measures we discussed previously (encryption, MFA, backups, monitoring, etc.), you’re likely meeting many of the security obligations in your field. Always keep an eye on industry news – for example, CISA (Cybersecurity and Infrastructure And if your industry has an information sharing group, it’s worth joining or at least keeping tabs on their alerts for threats hitting businesses like yours.
Case Studies: Recent Cloud Security Incidents & Lessons Learned
Sometimes the best way to drive home security lessons is through real-world examples. Let’s look at a few incidents that involved SMBs and cloud vulnerabilities, and see what went wrong and what we can learn:
Case 1: The Bogus Wire Transfer – Email Account Takeover at a Real Estate Firm.
A U.S. real estate development company, Wright Hotels, discovered it was missing $1 million from its accounts.
How did this happen? Attackers had quietly gained access to the company president’s cloud email account. They likely did this via phishing or guessing a weak password. Once inside the email, they monitored conversations and learned the firm’s money wiring procedures. The hackers then crafted a perfectly-timed fraudulent email, posing as the president, instructing the bookkeeper to wire funds to a new bank account (which actually belonged to the thieves). Because the email appeared internal and used details the bookkeeper expected, they completed the transfer. By the time the firm realized the president never sent that email, the money was gone overseas.
Lesson: This was a classic Business Email Compromise (BEC) facilitated by a cloud email takeover. To prevent it, the firm could have:
- Used multi-factor authentication on the email account. So, even if the password was stolen, the attackers wouldn’t get in without the second factor.
- Have a policy to verify any transaction requests above a certain amount (e.g. a quick phone call to the requester) could have stopped the fraud, even after the email was compromised.
- Train staff to spot red flags (“why is the boss asking me to wire money urgently to this unfamiliar account?”).
This case underlines that protecting cloud email access is critical, and that process controls (like two-person approval for large wires) are a necessary complement to technical security.
Case 2: Ransomware at a Cloud Provider – The Rackspace Outage.
In early December 2022, Rackspace – a major cloud hosting provider – suffered a ransomware attack that knocked out its Hosted Exchange email service for thousands of customers.
How did this happen? Many of those customers were small and medium businesses that relied on Rackspace’s cloud to host their company email. Suddenly, over the holiday period, these SMBs couldn’t access their email – some for days or weeks – and it turned out Rackspace had to shut down that portion of its service indefinitely. Even worse, it was reported that some customer email data was lost because it wasn’t fully recoverable from backups. For the affected businesses, this was a nightmare: they had outsourced email to the cloud for reliability, yet found themselves scrambling to recreate email accounts on other services, notify their clients through alternate means, and try to recover historical messages.
Lesson: First and foremost, using cloud services doesn’t mean you can forget about backups and contingency plans.
- Always maintain backups of critical cloud data that you control (for example, periodically export your email or at least have an email forwarding/archiving set up to a secondary location). That way, if your cloud provider has an incident, you’re not totally at their mercy.
- Evaluate the redundancy and security of key providers – in this case, many affected SMBs learned the hard way that Rackspace’s backups or incident response plans were insufficient. It’s wise to ask your cloud vendors how they would handle a disaster and if they’ve been through security audits.
- Have a basic business continuity plan: if one cloud service goes down, do you have a way to function temporarily? (E.g., keep a list of client contacts outside your email so you could reach them, use an alternate communication method, etc.)
For SMBs, the Rackspace incident was a wake-up call that the cloud is not invulnerable. The phrase “don’t put all your eggs in one basket” applies. Ultimately, trusting a cloud provider is fine, but trust with verification and backup is better.
Case 3: The Company That Literally Lost Everything – Code Spaces.
This incident is a bit older (2014) but it’s so dramatic and instructive that it’s worth revisiting. In a span of 12 hours, Code Spaces went from a functioning business to total loss. They announced they could not continue operations because nearly all customer data and backups were destroyed.
How did this happen? Code Spaces was a small hosting and collaboration platform for software developers – basically an SMB that provided cloud-based code repositories. They used Amazon Web Services (AWS) as their underlying cloud infrastructure. In Code Spaces’ case, a hacker gained access to their AWS management console – essentially the control panel to their entire cloud environment. The attacker did this during a distraction (a DDoS attack) and likely through compromising credentials (possibly an unused admin account or lack of MFA on the console). Once inside, the hacker attempted to extort Code Spaces for money. When Code Spaces didn’t pay, the attacker proceeded to delete everything: they wiped out virtual server instances, storage buckets, and crucially, all the backup data and machine snapshots
Lesson: There are several.
- Protect your cloud admin accounts ferociously – AWS (and other cloud platforms) now offer features like multi-factor authentication, API access keys with limited scope, and specialized roles. Use them. If Code Spaces had MFA on their root AWS account, the hacker likely couldn’t have gotten in so easily.
- Isolate and secure backups – “offsite” should ideally mean off the primary cloud or at least in an account the main admin can’t directly delete. Had Code Spaces kept independent backups (say, a read-only copy in a different cloud or on physical media), the attacker couldn’t have so easily destroyed all copies of the data.
- Follow the principle of least privilege. The attacker in this case had full admin privileges, but maybe they initially only got some credentials – one wonders if better internal segregation of duties could have limited the damage (though a determined attacker often goes for the jugular – the admin console).
For SMBs, Code Spaces illustrates that cloud doesn’t automatically mean safe – you have to configure and use cloud security features correctly. It also underscores the importance of preparing for the unthinkable. Losing all data is an extinction-level event, so build in failsafes to prevent that, such as immutable backups (backups that can’t be easily deleted) or third-party backup services that store data separately.
Each of these cases – a phishing financial fraud, a cloud provider outage, a full infrastructure breach – shines a light on specific aspects of cloud security. And in each, we see our earlier advice in action (or the consequences of not having it in action). For Wright Hotels, strict email security and verification processes were the remedy. For Rackspace’s customers, backups and multi-provider resilience were key. And for Code Spaces, it was about fortifying cloud administration and backup strategy. As an SMB, you may relate more to one scenario than another, but collectively they remind us that cyber incidents can hit anyone. The silver lining is that we can extract wisdom from these events to avoid repeating them.
Wrapping Up
All of the measures we discussed may feel like a lot to take in, but you don’t have to do everything at once. Think of these as protection layers that together make your cloud environment much safer. Even implementing a few key ones (say, MFA, backups, and employee training) will dramatically reduce your risk. To sum up, here are nine actions you can take to protect your business today.
Remember, security is a journey, not a destination. The threat landscape evolves, and so will your business and technology. Regularly review your risks (perhaps annually, or when you make big changes like adopting a new cloud service). Keep an eye on news or bulletins relevant to your industry, and learn from others’ mishaps (like the case studies we discussed).
Cloud technology can be a fantastic enabler for small businesses – and with solid security practices in place, you can reap its benefits with much less worry.
Related: Top Cybersecurity Certifications for 2025
Related: How To Become a Data Scientist